WebRTC is an API available for Google Chrome, Mozilla Firefox and Opera. The purpose of the API is to enable a direct link between web browsers when using services like VoIP and file sharing peer-to-peer.
A small piece of JavaScript code was recently released, enabling people to access the internal and external IP addresses of other users despite them using proxy and/or VPN.
How do you protect yourself?
This is a very serious issue since many users trust their VPN, which has always been the obvious choice for anonymity and security on the Internet. Since WebRTC is seldom used, we recommend that you disable it immediately.
Block WebRTC in Firefox
Install OVPN's browser extension that blocks WebRTC.
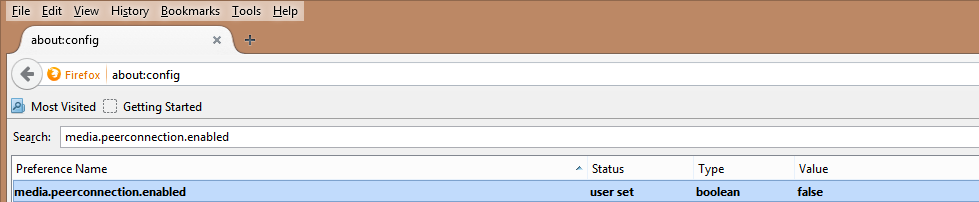
You can also visit about:config in the browser and search for media.peerconnection.enabled and change the value to False by double clicking this line:
Block WebRTC in Chrome
Install OVPN's browser extension that blocks WebRTC.
How does WebRTC work?
WebRTC sends so-called STUN requests, returning your network adaptor’s internal and external IP addresses. Since these STUN requests are made through UDP, they are not transported over HTTP or SOCKS, which both are based on the networking protocol TCP. This is what a request looks like: 
Plugins like Ghostery, Adblock, Disconnect and Flashblock can’t block these requests.
It’s worth noting that this is only a problem when using Windows. If you are using OSX or Linux, your internal IP address is still exposed, but not your public IP address, making it much safer. However, if you are using Firefox in OSX or Linux, we still recommend that you disable WebRTC.
Verify that WebRTC is disabled
After installing the plugin or if you decided to manually disable WebRTC, it’s a good idea to verify that it’s working as intended.
The easiest way is by going to our dashboard where we run a WebRTC test for you, or directly to our WebRTC leak test page.

