This guide is directed for advanced VPN users.
VPN and Tor are two different network protocols that can offer good anonymity. There are of course pros and cons for both of them, and each of them is good but for different intentions.
Here are two pros and two cons for both Tor and VPN protocols:
Tor - Pros
- Offers anonymity by tunneling the traffic through several proxy-servers.
- Free and easy to use
Tor - Cons
- Can be very slow
- "Evil" exit nodes searching for plain text and manipulates traffic
VPN - Pros
- Offers strong encryption with OpenVPN
- Can be very fast
VPN - Cons
- Based on trust of the provider: you can only make sure you are anonymous if you trust your VPN service provider fully.
- Usually not free
Optimal anonymity by mixing Tor and VPN protocols
Using a VPN together with Tor is not hard. You can use your VPN service of choice and use Tor Browser Bundle as your web browser, but it’s not perfect.
The reason for this is that the last node in Tor can still read the plain text (for example, visits from HTTP and FTP) and thus manipulate it. In addition, your VPN provider can see your real IP address. The only benefit of using this setup is that your ISP only sees VPN traffic and you prevent IP leakage from the Tor network.
VPN through Tor makes you extremely anonymous and secure
If you let your VPN traffic go through the Tor network first, you get the best of both worlds. You get total anonymity, and this method is seen as the most optimal one. Below you can find a picture illustrating this method:

If you use this method, you remove the dangers with Tor and also become anonymous to your VPN provider. The exit node will see only encrypted VPN traffic. The exit node also doesn’t know where you are coming from and can only see that you are going to connect to a VPN server. The VPN service provider receives traffic from the exit node and thus cannot know the client’s initial IP address.
OVPN has a development VPN servers which we use to debug and test new features on. The server (DEV01), which is not used by any of our clients, functions exactly like our other VPN servers except that it logs data so we can troubleshoot issues. Below is an example log entry of the information that a VPN servers is provided when running a VPN service through Tor:
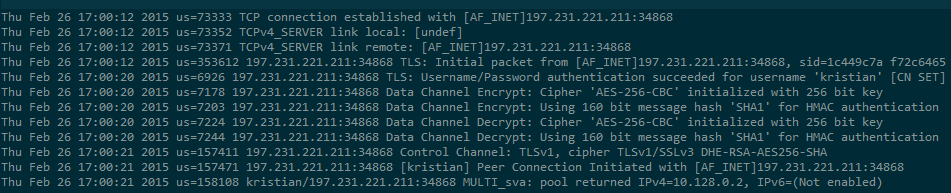
The only things being logged are the username, the IP address, and the port number. As we can see in the illustration above, the IP address is "197.231.221.211," which is the IPredator exit node (exit1.ipredator.se). Since these are logs generated by OpenVPN, it means that the traffic is not decrypted until it reaches the VPN server. In other words, the exit node can’t see any traffic regardless if you browse with plain text such as HTTP or FTP.
VPN through Tor is possible with OVPN!
We recently added this functionality as many of our customers asked for it. In order for it to work, we need to have TCP support on our servers, which was ruled out as it’s slower than UDP. From now on, customers can use TCP through port 443 on VPN05.
How can I get it to work?
If you choose to tunnel VPN traffic through Tor, you need to be aware that your connection is going to be a lot slower than normal. The speed is decreased considerably as Tor routes your traffic through a large number of servers.
If you are using Linux, the installation process is simple as the package is usually available through the package handler (apt-get install tor). If you are using Windows, you will need the Tor Expert Bundle, which can be found here.
Once the Tor Expert Bundle is downloaded, extract the archive to your desktop. Double-click Tor.exe and wait for about a minute (as Tor needs to connect to the network).
You then need to exit Tor. You should put your torrc file in %appdata%\tor and the file content should be:
SocksPort 127.0.0.1:9050 PreferSOCKSNoAuth
Run Tor.exe again and connect as you would usually do to OVPN. If the connection is established, go to www.myip.is and make sure that OVPN's IP address is shown. If it is, then you are successfully using VPN through Tor.
Linux and OSX
You can install for OSX via brew. If you don’t have brew installed, you can write the following command in the terminal:
ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"Once the installation of brew has finished, you can install Tor with brew using the following command:
brew install torFor Linux, Tor is available in most distributions. For Debian/Ubuntu, you can install Tor by running the following command:
sudo apt-get install torAfter the installation process, you can run Tor via the terminal (after changing the torrc file), and then connect to OVPN with the above-mentioned configuration file.
David Wibergh
